OpenVPN server on Truenas Scale
Published on
The setup
So you have a truenas scale server, which holds all your most precious data. And chances are this is a machine you want to be able to access from anywhere because of this. Maybe even you want to actually utilize the sharing capabilities of your NAS, like Samba to use your data.
Good use of resources would be to turn you NAS into a VPN server. This is done really easily on Truenas scale specifically: basically one press of a button and you are done.
So I assume you already have you OpenVpn server up and running and can connect to the Nas via it.
 In my case the 10.0.0.0\24 network is a VPN and the 192.168.1.0\24 is a remote LAN. In your case ranges can differ.
In my case the 10.0.0.0\24 network is a VPN and the 192.168.1.0\24 is a remote LAN. In your case ranges can differ.
The problem
But what if you now want to be able to access any device in that network. Like if it’s your home network, and you have a couple of useful devices there which you don’t want or cant connect to the VPN individually. So our goal here is to be able to connect to 192.168.1.1 via VPN while only the 192.168.1.5 is connected to the VPN (a VPN server in our case)
The solution
In order to access the LAN of your Truenas Scale server you’ll need to enable an ip forwarding. Between the interfaces on the NAS. This will allow traffic to flow freely from the VPN network into LAN and back, giving you easy access to the resources in the LAN.
All the actions we require need to be done from advanced system settings so navigate to System Settings -> Advanced
- Add a sysctl variable named
net.ipv4.ip_forwardwith value1and enabled checkbox ticked. - On a neighboring panel called ‘Init/Shutdown Scripts’ add following 3
Commands with the names you will understand:- Command:
nft add table ip nat, When:Post init - Command:
nft 'add chain ip nat prerouting { type nat hook prerouting priority 0 ; }', When:Post init - Command:
nft 'add chain ip nat postrouting { type nat hook postrouting priority 100 ; }', When:Post init
- Command:
- We also need a 4-th
Command, but you need to know 3 values in order to form it correctly. The easiest way to do it is to navigate toSystem settings->Shelland execute theip addresscommand. you can find the necessary values by searching for IPs you recognize as the on from the LAN and the one from the VPN networks. The values you need are:
you can find the necessary values by searching for IPs you recognize as the on from the LAN and the one from the VPN networks. The values you need are:
- Name of the openvpn network interface. Mine is
openvpn-server - Name of the lan interface. Mine is
enp2s0 - The VPN subnet CIDR. Mine is
10.0.0.1/24
- Name of the openvpn network interface. Mine is
- Add the 4-th command replacing my values with yours. The Command will be
nft 'add rule nat postrouting iifname openvpn-server oifname enp2s0 ip saddr 10.0.0.1/24 masquerade', and when the field isPost init - THe last and really optional step is to make your clients know how to route traffic to your server’s LAN. In order to do that - navigate to the
Network->Open VPN->Serverand addpush "route 192.168.1.0 255.255.255.0"toAddtional parametersfield.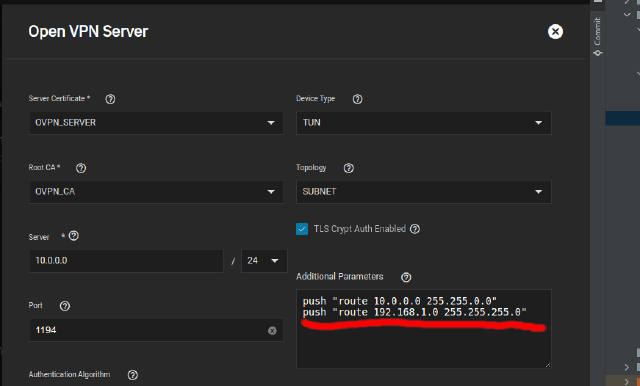
Verification
Connect to the VPN from your client and try to ping or access in any other way the ip from your server’s LAN (192.168.1.1 in my case).
 It works, yay!
It works, yay!